Jarbas 渗透测试笔记
渗透过程
拿到靶机开机第一件事就是就是找到靶机,先用 nmap 扫一下同一网段的机子
$ nmap 10.0.2.0/24
Starting Nmap 7.95 ( https://nmap.org ) at 2025-01-21 02:01 EST
Nmap scan report for 10.0.2.1
Host is up (0.000034s latency).
Not shown: 999 closed tcp ports (reset)
PORT STATE SERVICE
53/tcp open domain
MAC Address: 52:54:00:12:35:00 (QEMU virtual NIC)
Nmap scan report for 10.0.2.2
Host is up (0.000063s latency).
Not shown: 993 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
139/tcp open netbios-ssn
445/tcp open microsoft-ds
631/tcp open ipp
902/tcp open iss-realsecure
24800/tcp open unknown
MAC Address: 52:54:00:12:35:00 (QEMU virtual NIC)
Nmap scan report for 10.0.2.3
Host is up (0.000042s latency).
All 1000 scanned ports on 10.0.2.3 are in ignored states.
Not shown: 1000 filtered tcp ports (proto-unreach)
MAC Address: 08:00:27:A3:71:23 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Nmap scan report for 10.0.2.15
Host is up (0.000049s latency).
Not shown: 996 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
3306/tcp open mysql
8080/tcp open http-proxy
MAC Address: 08:00:27:FE:DD:8E (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Nmap scan report for 10.0.2.5
Host is up (0.0000020s latency).
All 1000 scanned ports on 10.0.2.5 are in ignored states.
Not shown: 1000 closed tcp ports (reset)
Nmap done: 256 IP addresses (5 hosts up) scanned in 2.32 seconds
访问两个开放了 80 端口的机子可以知道目标机器是10.0.2.15
找到目标后进行更进一步的扫描
$ nmap 10.0.2.15 -sV -sT -O
Starting Nmap 7.95 ( https://nmap.org ) at 2025-01-21 02:03 EST
Nmap scan report for 10.0.2.15
Host is up (0.00049s latency).
Not shown: 996 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
80/tcp open http Apache httpd 2.4.6 ((CentOS) PHP/5.4.16)
3306/tcp open mysql MariaDB 10.3.23 or earlier (unauthorized)
8080/tcp open http Jetty 9.4.z-SNAPSHOT
MAC Address: 08:00:27:FE:DD:8E (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.14
Network Distance: 1 hop
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.00 seconds
获取到有 OpenSSH 7.4 Apache httpd 2.4.6 MariaDB 10.3.23 Jetty 9.4.z-SNAPSHOT 等服务,系统版本是 Linux 3.2 - 4.14 ,报告中也可以知道是 CentOS 这个发行版(其实启动靶机的时候就知道了)
除了 TCP 要扫,UDP 也要扫
$ nmap 10.0.2.15 -sU
Starting Nmap 7.95 ( https://nmap.org ) at 2025-01-21 02:05 EST
Stats: 0:00:52 elapsed; 0 hosts completed (1 up), 1 undergoing UDP Scan
UDP Scan Timing: About 6.20% done; ETC: 02:19 (0:13:22 remaining)
Stats: 0:02:18 elapsed; 0 hosts completed (1 up), 1 undergoing UDP Scan
UDP Scan Timing: About 14.30% done; ETC: 02:21 (0:13:53 remaining)
Stats: 0:07:01 elapsed; 0 hosts completed (1 up), 1 undergoing UDP Scan
UDP Scan Timing: About 40.78% done; ETC: 02:22 (0:10:13 remaining)
Stats: 0:15:54 elapsed; 0 hosts completed (1 up), 1 undergoing UDP Scan
UDP Scan Timing: About 88.06% done; ETC: 02:23 (0:02:09 remaining)
Nmap scan report for 10.0.2.15
Host is up (0.00064s latency).
Not shown: 996 closed udp ports (port-unreach)
PORT STATE SERVICE
68/udp open|filtered dhcpc
539/udp open|filtered apertus-ldp
998/udp open|filtered puparp
5353/udp open|filtered zeroconf
MAC Address: 08:00:27:FE:DD:8E (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 1114.07 seconds
并没有什么特别有用的价值,目前已知有两个站点,一个在80端口,一个在8080端口
访问发现一个是网站主站,一个是管理网站的
两个站点都可以试着目录爆破一下
$ gobuster dir -u http://10.0.2.15 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x html,php
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.0.2.15
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: html,php
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 32808]
/.html (Status: 403) [Size: 207]
/access.html (Status: 200) [Size: 359]
/.html (Status: 403) [Size: 207]
Progress: 429860 / 661683 (64.96%)[ERROR] Get "http://10.0.2.15/60411.html": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://10.0.2.15/60411.php": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://10.0.2.15/Yasasoft%20Dvd%20To%20Vcd%20Avi%20Divx%20Converter%20Magicdvdripper%20v3": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://10.0.2.15/60411": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://10.0.2.15/Yasasoft%20Dvd%20To%20Vcd%20Avi%20Divx%20Converter%20Magicdvdripper%20v3.php": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://10.0.2.15/10691": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://10.0.2.15/10691.html": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://10.0.2.15/10691.php": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://10.0.2.15/74516": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://10.0.2.15/74516.html": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
Progress: 661680 / 661683 (100.00%)
===============================================================
Finished
===============================================================
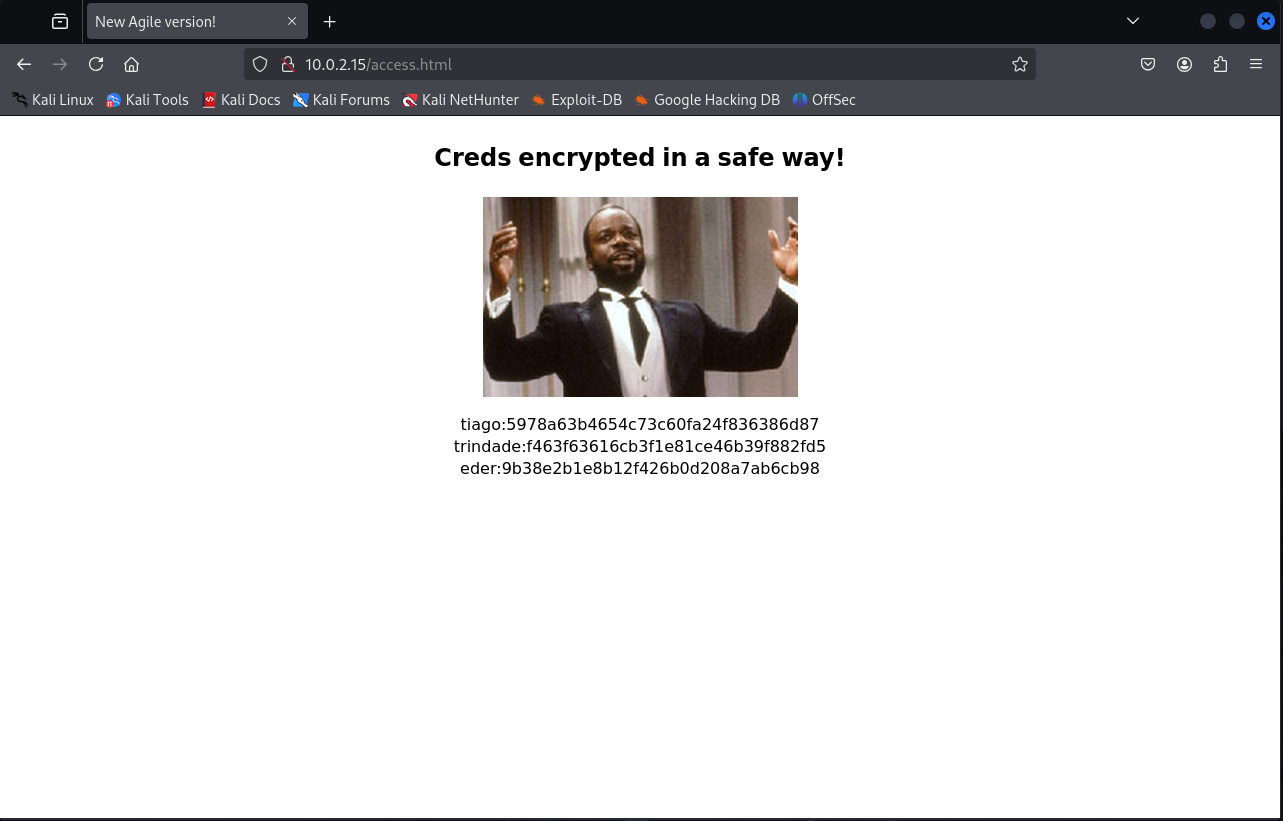
可以发现有一些比较有趣的页面,access.html
(PS: 刚开始扫描没有加 -x 参数,没有扫到目录,加上 -x 以添加后缀后就可以扫到了)
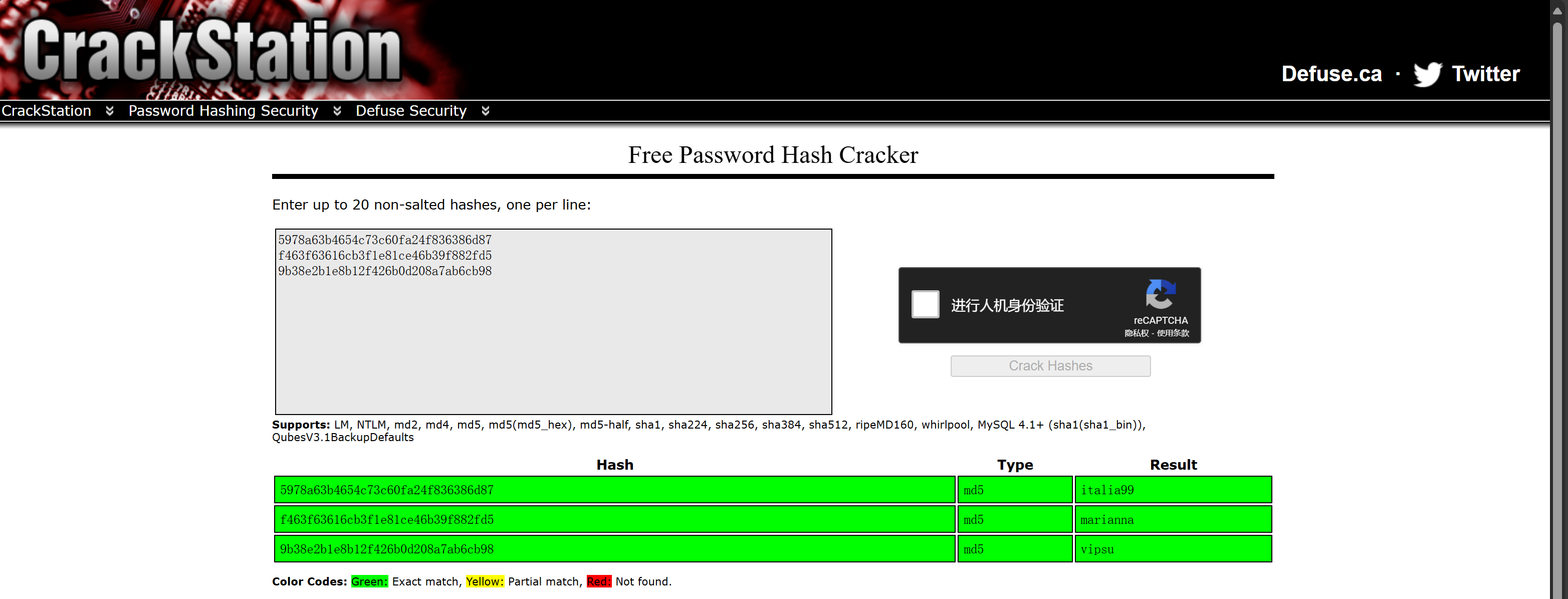
访问 access.html ,可以看到有三个像是 md5 加密值的东西
找解密的网站找一下,发现都能找到
貌似是账号和密码的对应关系,试着在 8080 端口的站点登录,可以发现 eder 这串可以登入
网站使用的是 Jerkins,可以通过构建任务来执行 shell 命令
利用此来反弹 shell
反弹指令执行前要先开启监听
得到 shell 后先查明用户情况
可以看到大部分都是功能性的账户,所以提权的目标是 root 用户
检查一下其他的地方,比如 crontab
发现 crontab 有在用 root 身份每五分钟执行一个脚本,可以通过修改脚本来获取 root 用户的 shell
等待最多五分钟即可得到 root shell,同样的,也要提前开启监听
拿到 shell 后就可以试着找 flag 等文件了
总结
- 操作上:
- 在扫描时没有进行全端口扫描,只扫描了低位端口,
-p-参数没有加。虽然有很多服务默认端口都在低位,但不扫描高位的话容易错过可以利用的地方。 - 目录爆破可能需要备一些字典
- 8080 端口站点也可以尝试字典爆破
- 在扫描时没有进行全端口扫描,只扫描了低位端口,
- 过程难点:
- 想获取 root shell 的时候有点不好找如何提权,这需要熟悉常见的可利用提权方法 渗透测试之提权篇一 渗透测试之提权篇二(Linux 提权) 渗透测试之提权篇三(Windows 提权)
- 除了常用提权方法,也需要熟悉常用的反弹 shell 手段 渗透测试之反弹shell合集
- 其它手段:
- Jerkins 有许多可以利用的漏洞,本次渗透可以尝试利用
CVE-2019-1003000
有关更多 Jenkins 的漏洞 - 一些奇技淫巧:通过编辑 grub 以进入 root shell,因为在一般的渗透测试中比较难拿到机器的物理控制权限,所以比较罕见(
黑客潜入服务器机房戏码,不过 grub 也可以上密码来着) - 端口扫描时还有一个开放的 3306 端口,使用的是
MariaDB,可以尝试查找可利用的漏洞
- Jerkins 有许多可以利用的漏洞,本次渗透可以尝试利用
 琼公网安备46010602001577号
琼公网安备46010602001577号